Cisco Switch Password Recovery - In Few Easy Steps
Posted by Ahsan Tasneem | 3:02 AM | cisco, How To | 1 comments »
Note: This article is based on a
Cisco Catalyst 2900, 3500XL, 2940, 2950, 2955, and 3550 switches, for other you
can search and find them easily using any search engine
To recover a password on a Cisco switch, you will have to be connected to the console port of the Cisco switch using 9600 baud, 8 bits, no parity, 1 stop bit, and xon/xoff flow control. I recommend using Hyperterminal that comes with Windows XP.
Once you are connected and see something on the terminal window when you press enter, unplug the power cable. Next, hold down the mode button on the front, as seen in the photo below, and connect the power cable.
On a 2900, 3500XL or 3550 (like the one shown) release the mode button after the 1x port LED goes out. On a 2940 or 2950 switch release the mode button after the stat light goes out. On a 2955, press the break key (ctrl-break on Windows) when you see the message that the switch will autoboot.
You should now see something like this (taken from a 3550 switch):
Notice that it says that the password-recovery mechanism is enabled.
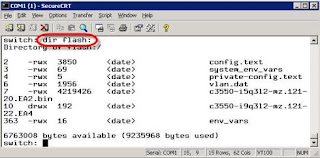
Now type dir flash: and press enter. You should see something like this:
copy flash:config.text system:running-config
Via: http://www.petri.co.il
To recover a password on a Cisco switch, you will have to be connected to the console port of the Cisco switch using 9600 baud, 8 bits, no parity, 1 stop bit, and xon/xoff flow control. I recommend using Hyperterminal that comes with Windows XP.
Once you are connected and see something on the terminal window when you press enter, unplug the power cable. Next, hold down the mode button on the front, as seen in the photo below, and connect the power cable.
On a 2900, 3500XL or 3550 (like the one shown) release the mode button after the 1x port LED goes out. On a 2940 or 2950 switch release the mode button after the stat light goes out. On a 2955, press the break key (ctrl-break on Windows) when you see the message that the switch will autoboot.
You should now see something like this (taken from a 3550 switch):
Notice that it says that the password-recovery mechanism is enabled.
Now type load_helper and press enter. You should see
something like this:
Now type dir flash: and press enter. You should see something like this:
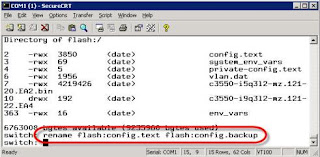
The config.text file is what stores the administrative password that is
keeping you from logging into the router. To get rid of this file, use this
command:
rename flash:config.text flash:config.backup
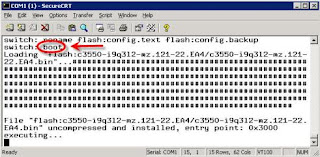
Next, boot the switch using the boot command, like this:
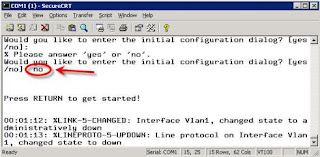
Once the system is booted, you will be asked if you want to
enter the initial configuration dialog. Say no
and press enter.
Next, enter enable mode with the en or enable command. Then, type the
following commands:
rename flash:config.backup config.textcopy flash:config.text system:running-config
After each command, you will be prompted to confirm the name of the
destination file. Do this by pressing enter each time.
Go into global configuration mode by typing config terminal.
Next type no enable secret.
Now you can reset your enable password to whatever password you want. In the
example below, we used the enable password NetInsider to set
the password to NetInsider.
Exit out of global configuration using the exit command and
save your configuration with the copy running-config startup-config
command. You will be prompted to confirm the name of the destination file.
Press enter.
You have successfully reconfigured your switch’s enable password using the password recovery procedure. Even better, you were able to do this while preserving the entire switch configuration.
This must be really easy for those who already knew but I have post this
article for those who either do not know how to recover the password or have
forgotten with the passage of time. You have successfully reconfigured your switch’s enable password using the password recovery procedure. Even better, you were able to do this while preserving the entire switch configuration.
Via: http://www.petri.co.il
Subscribe to:
Post Comments (Atom)










I will bookmark your blog and take the feeds additionally? I’m satisfied to find so many helpful information here within the put up, we want work out extra strategies in this regard, thanks for sharing..
VMware Training in Chennai